DESCRIPTION
- Quick, Defeats Bad Calls in ½ Second
- No Additional User Sign-On Delays
- Deceptively Easy To Use
- No User Training Required
- Transparent to the Hardware and Software
- No AC Power or Batteries Required
- Field Programmable (Change or Add)
- Any "Group Unit" can Act as a Lock or Key
- Over 1 Billion Handshake Combinations that Change with each Call
Introduction
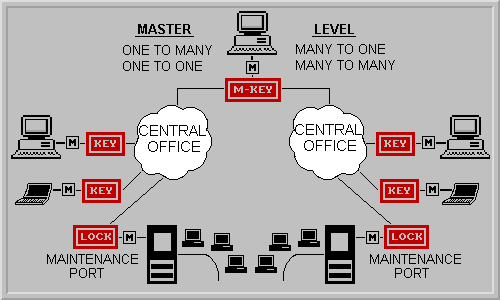
The Challenger P2 BAS (Bi-Level Access System) was primarily designed to provide
absolute authentication type of security for remote dial-line maintenance
applications. However, it may also be used in any application where secure
groups of modems may also require a Master Level of access. It allows the
subject equipment to be securely accessed by its own group of users as well as
by the manufacturer or third party maintenance firm through a "Master Key"
that has access to all of the secure user groups.
Operation
The entire system operates on a LOCK and KEY principle similar to Locks and Keys
in the home or office. The matchbox sized hardware boxes (Locks and Keys)
connect to the analog side of the operative modems with RJ-11s. They are
completely independent of the hardware (internal/external modems or terminal
equipment) and the associated software. No AC power or batteries are required.
The units derive their power from the TelCo lines when they become active.
Any call received by a modem with a Lock connected will be challenged for the
presence of a proper "Group Key" or "Master Key" at the calling
end. If the Key is present, the call will be allowed to progress transparently
with no additional delay or operator intervention. However, if there is no Key or
a wrong Key is detected, the call will be defeated within a ½ second and it
will never be identified as a modem answered call by war dialers or other equipment.
This allows the subject modems to remain powered on and available without fearing
that hackers, ex-employees, or wrong numbers may gain access to the system.
There are over 1 billion handshake combinations between the units that change
with each call, resulting in an extremely high degree of authentication.
Programmable
Each of the P2 units in the group can function as a Lock or a Key. The Locks,
automatically become Keys when used to dial to another member of their group.
They are transparent when dialing the outside world. A Master Lock within each
"Secure Group" can also be used to change the security code or program
additional units within the group. However, the Master Key maintains access to
any of the Locks in any group through another level of access that is factory
programmed. Any of the "secure user groups" can have as many Locks or
Keys as may be necessary and a "secure system" may have an unlimited
number of unique user groups.
In spite of its small size and ease of use, the P2 BAS represents a very
flexible and very effective authentication system that is deceptively simple to
use. It can be used alone or as a hardware front end to established password
systems providing "two factor authentication" in stationary or mobile
applications. It is a great way to quickly secure dial access without requiring
any additional costly user training. Often the savings in training cost can
justify the cost of the product.
For more information on the Challengers, check out the Challenger
Family Page. Also check out security comments and questions that were
"Heard at the Booth".