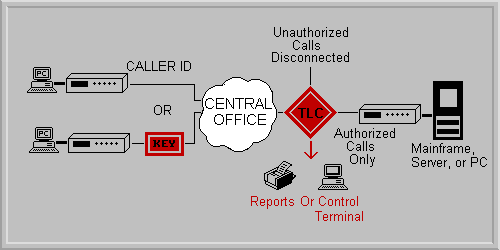
SECURITY through
- Caller ID - Challenger Keys
- Audit Reporting
- Use for Remote, Mobile, or Cell Phone Users
DESCRIPTION
The Telephone Line to Computer Interface has a number of uses.
However, it was primarily designed to be used for AUTHENTICATION TYPE SECURITY
and AUDIT TRAIL REPORTING for dial telephone lines. It can be used for either
or both.
It provides up to two security options.
- CPS's CHALLENGER hardware keys and
- CALLER ID.
This makes it an effective authentication device for the stationary remote user
as well as the mobile user. The Caller ID feature addresses authentication
requirements for cell phones.
It can be used in large commercial environments with a number of TelCo lines,
or in a small office environment with only a few lines. One unit is required
for each line. It can also be used in the home to eliminate the disturbing
rings from unwanted nuisance calls.
SECURITY
When used in the SECURE MODE, the TLC challenges all inbound calls for the
proper means of identification from the caller. It provides two levels of
security:
- The CHALLENGER HARDWARE KEYS provide the quickest and highest level of
security. The Keys are small match box sized devices that connect to the
callers modems with standard RJ-11 type connections. Unauthorized calls that
fail to meet challenge/response are aborted in less than one half second and
are not recognized as modem answered calls by hackers. The customer can program
a separate user ID number into each Key, which can be used for further audit
purposes, if required.
- The CALLER ID security option matches the inbound Caller ID number against a
database of authorized numbers prior to allowing the ring through. The database
is entered from the PC. It can accommodate up to 50 valid Caller ID numbers.
REPORTS
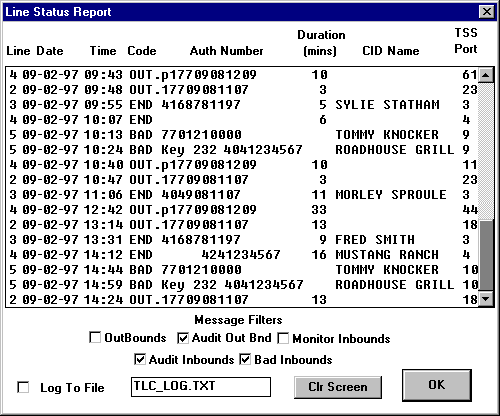
The TLC also provides a time/date stamped detailed report (pictured below) of
both inbound and outbound calls. Inbound calls include the Caller ID number or the
CHALLENGER KEY ID number, if used, as well as the call duration. This event
log is transmitted to a printer, PC or any serial device connected to the RS-232
port as it occurs.
The unit is easy to operate. It connects to the analog side of the receiving
modem, or other analog devices and to the RS-232 port on a PC. Multiple units
may be stacked together or "book end stacked" on a 19" rack
mount shelf. The concatenation port supplies power as well as event information
to subsequent ports.
SPECIFICATIONS
TELCO LINE to COMPUTER INTERFACE (TLC)
Item No SWTCI Price $295.00
Physical 5.5" W x 3.5" D x 1" H, 1 lb.
Connectors (2) RJ-11 TelCo, (2) RJ-45 RS-232
LEDs (4) Power, Mode, Key Program
Switches None
Bell None
Cable (1) 5' RJ-11 Phone Cable,
(1) 3' RJ-45 Cable
Adaptor (1) RJ-45 to DB-9 Female RS-232
AC Power Wall Mount 9VAC 1A, 115V/60Hz
OPTIONAL SECURITY KEY
Item No SWTTC-R
Quantity 1-5 6-10 11-25 26-50
Price each $79.00 $74.00 $65.00 $55.00
Physical 1.5" W x 3" D x .75" H, .25 lbs.
Connectors (2) RJ-11
LEDs (1) Verify Connection
Switches (1) Manual 8 Position Rotary
Bell None
Cable (1) 15" RJ-11 Phone Cable
Adaptor None
AC Power None
|
|
Computer Peripheral Systems, Inc.
5096 Bristol Industrial Way, Suite B
Buford, GA 30518
Sales
1-800-888-0051
8:30 AM - 5:30 PM EST
Technical Support
(770) 945-0643
8:30 AM - 5:30 PM EST
Fax
(770) 945-9342
E-Mail
sales@cpscom.com
©
Copyright 1996-2003
Computer Peripheral Systems, Inc.
This file last modified September 2, 2003
|