The following are some of the Comments (C) and Reponses (R) that were
"heard at the Booth" at some of the security conferences and shows that
we attended. They reflect the concerns of those who are using Dial Security as well as
those who may be investigating it for the first time.
Most of the suggested solutions are based on our CHALLENGER
family of hardware dial security products. It demonstrates the flexibility and broad
range of the family.
Concerns change as technology evolves, but the old ones don't seem to go away. Some of
the newer concerns and product solutions are added at the end of each section.
If you would like to include your comment or experience, click here
 and we will add it to the e-mail FEEDBACK section.
and we will add it to the e-mail FEEDBACK section.
STANDARD CHALLENGER -
CHALLENGER P2 -
CHALLENGER P2 BAS -
CHALLENGER TT -
CAS -
TLC -
SP-RRC -
K-RRC -
MRS -
FTS -
232-PSS -
MINI FIREWALL -
ENFORCER -
TSS
GENERAL COMMENTS
C. "Our users don't like our current sign-on security system with the key
pads on the credit cards. It takes too long to sign-on; an average of over 4 minutes.
We got the system years ago, but now we have 50 times as many sign-ons and it adds up.
We need to streamline the procedure."
R. Use a CHALLENGER system. The user simply connects
a match-box sized security KEY to his modem and uses it. No further intervention is
required.
C. "We don't need a national defense type of security, just something that
is easy for us and easy for our users, but we want it to work too... and not too
expensive."
R. Use the CHALLENGER P2. They are only $79.00
each. Buy as many Challenger P2 Auxiliaries as are required for your application. They
are deceptively simple to use and with over a billion handshake combinations that change
with each call, you may be closer to a national defense level of authentication than you realize.
C. "We had enough trouble getting the software to work and training the
users to use it. I don't want to go through that again for the sake of security.
I just need something easy, that I can put in the mail and the secretaries can
connect."
R. The CHALLENGER KEYs have two RJ-11 connectors.
Anyone can connect them; from that point they operate transparently.
C. "With your Challenger, we can skip a lot of the of our initial software
security procedures and just use it for auditing. It works great."
C. "We use passwords. I don't want to change our whole system. I just need
something that will work with it. A front end of sorts."
R. Passwords are quickly becoming obsolete, but combining them with a hardware
system can make them a thousand times more effective. Hardware such as
CHALLENGER LOCKs and KEYs will also provide the
"something you have" aspect to meet the requirement for two factor
authentication.
C. "We don't have much control over our users. They share passwords. One
password was used from Chicago and LA within the same half-hour. This makes our
audit reports useless. I want something they have to carry with them."
R. Give them CHALLENGER KEYs. They can't get into
your system without them. Plus your audit reports can tell you if the password and
User IDs in the KEYs match. What was that user's name? O.J.?
C. "The bank auditors busted me for having a dial modem on our mainframe.
I only turn it on at night, so I can fix any problems from home. What do you
have that will pacify them?"
R. A simple CHALLENGER P2 should do the trick.
C. "Attacks are happening in micro seconds, our current software only
deals with it after the fact."
R. Use STANDARD CHALLENGER hardware on your modems,
the attacks will be defeated before they happen. That should be quick enough. It provides
a pretty good audit trail too. No sense in dealing with attacks after they happen.
A much better solution is to prevent them.
C. "Our information may not be useful to anyone else. I just don't want to
be fair game to every wacko with a modem."
R. Unfortunately, the number of wackos with modems is increasing, but
CHALLENGER LOCKs and KEYs will stop the rascals.
C. "I want something that will work on all of my platforms. I don't want
to have to change it as my software changes."
R. The CHALLENGER LOCKs and KEYs connect to the
analog side of the operative modems so they don't care what type of modem they are
connected to or what kind of hardware or software is on the other side of the modem.
C. "We don't want to deal with a security breach. We want to avoid it, but
without driving our users crazy."
R. CHALLENGERS are just the ticket for you. They
avoid confrontations with unauthorized callers and are completely transparent to the
authorized callers.
C. "I wonder how many bogus attempts are occurring on my lines. Can your
system tell me?"
R. The event log on the STANDARD CHALLENGER
can supply that information. It will give you the time and date of each bogus attempt
on each line. We also have some other products that can report the Caller ID of the
caller. If that is of interest, look at the TelCo Line
to Computer Interface (TLC).
C. "Our insurance company said that they wouldn't raise our rates if we
got some better security on our dial lines. What do you have that is cheap and
easy that will satisfy the insurance guys?
R. The CHALLENGER P2. They are $79.00
each. You will have to do the math.
C. "We use PC Anywhere and allow our staff to dial in, but some PCs have
sensitive information."
R. Use the CHALLENGER P2 to provide authenticated
access. If the sensitive information is on a server, we also have another product called
a MINI FIREWALL that will simply disconnect the PC from
the LAN when the modem is in use. It is only $85.00.
C. "(School System) The word is out! Everybody is using dial access to our
server for access the Internet. Never a free line. We have to restrict access
some how."
R. Give students a CHALLENGER KEY. Let them check
it in and out like a library book. Put a max call time in the key.
C. "We have a Fire Wall between our server and the public server, but some
users are using their own modems to dial in behind it. This leaves us
vulnerable."
R. This has to be addressed at the wall plates or in the wire closet.
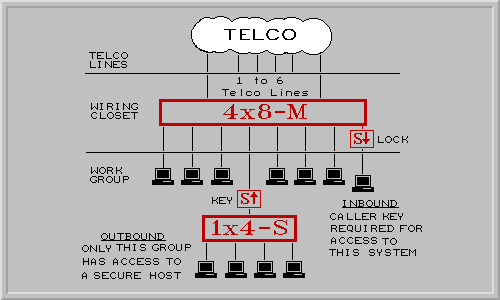
C. "How can I provide security at the desk top or the work groups level
with your products?"
R. Combine the CHALLENGER with our
Telephone Line Sharing Switches (TSS). You can
place a CHALLENGER LOCK or KEY in the wire closet on each telephone line or
before a work group. The possibilities are amazing.
C. "We get some financially sensitive FAXes. I want to be sure the
signature matches the sender's ID."
R. The CHALLENGERS can be used with FAXes as
well as with modems. Connect them in the same manner. No FAX will get through
unless there is a CHALLENGER KEY connected to the sending machine and the user ID
in the KEY can be matched against the signature.
C. "We switch our voice lines to modems at night to down load print files.
Many times we get a lot of crap in the morning and no print files. I think
someone has found our modems and is messing with our system."
R. Put a couple of CHALLENGER P2 on one of
the lines to see if the problem clears up. It will save a lot of speculation.
C. "We have 16 sites around the country that occasionally dial each other
during the day and transfer some files at night. What can we do to secure those
modem lines?"
R. Use the CHALLENGER P2. It serves as
a LOCK on all of your modems, but turns into a KEY when outbound calls are placed to
another LOCK secured system; or other non-secured system. They are match-box sized units
with two RJ-11 connectors. Just send them to your sites. Anyone can install them.
C. "Well Telecommuting has finally hit xyz Co. As the first step, what
do you have to verify legitimate callers?"
R. The STANDARD CHALLENGER is the standard
product solution for this application. Each caller has a hardware Key connected to
their modem. If they go on the road, they can take it with them. If they always
call from home, you might look at something that can screen calls based on Caller ID.
This is a little less secure, but it saves the cost of the hardware Keys. The
TLC can screen calls based on both Caller ID and hardware
Keys so it can be used for the mobile callers as well as those from fixed locations.
C. "We have a policy that no PC can have a modem and a NIC card installed.
But I know some users are bringing in their own modems and are surfing the net. It
scares the crap out of me knowing that they are connected to our network while this
is going on."
R. The MINI FIREWALL is what you are looking for.
It is a simple low cost product that will disconnect the PC from the LAN when the modem
is in use. Use the wall plate version so they cannot easily bypass it. The
ENFORCER version of this product requires
them to run a software program prior to re-establishing the LAN connection; if they don't
have this program they will have to ask you. Then you got them! You might also review
their temp internet files at that time so you know where they have been. The word will
soon spread.
C. "I know that some of our employees bring in their own modems so they
can dial into their PCs at night. How can I prevent these rogue modems from receiving
inbound calls?"
R. Get one of our Telephone Sharing Switches (TSS 2x8 or 4x8)
and connect their phone lines, in the wire closet, to the "station ports" that cannot
receive inbound calls (3-8 or 5-8). This will still allow them to use their modems to
dial out from that location, but not receive inbound calls.
C. "We just implemented dial security for some of our telecommuters and
for our field agents. We used xxx ID cards where the caller has to interact with a
control unit at the host site by entering randomly changing codes that appear on a
credit card if you press the right buttons. What a mess! We give them four minutes
to sign on and I think that I have to raise it to seven minutes. Some people never
get on. We have a lot of this equipment on order, but I think I can send it back.
It's more than just a learning curve. It's just too complicated for the level of
personnel and the environment that we intended it for... and to think, we paid a
consultant for this recommendation."
R. I know the system to which you are referring. One of our customers did a
study of our equipment (STANDARD CHALLENGER) verses
theirs. With ours, the number of successful sign-ons on the first attempt increased
92% and the average time to sign-on dropped from 3.3 minutes to 30 seconds (including
modem training time). You haven't yet hit the dead battery syndrome either. I also
heard that they are also licensing the use of these cards for a certain time. Is
that true? Or should I ask your consultant? I hope you didn't pay him yet.
C. "To save phone lines, I want to poll all of my salesmen's PCs at
night in their homes. This means that they will have to leave them on. Which means
that they are open for anything. What do you have?"
R. Put a CHALLENGER P2 AUXILIARY on each of
the salesman's modems and another on each of the polling lines. The salemen will also
be able to call you during the day on a secure basis if that may be a requirement.
C. "We use war dialers to scan our company's lines to enforce our
policy against open modems. What do you have that I can offer the department manager
as an alternative to taking out the modem when I find them?"
R. He can put a CHALLENGER P2 AUXILIARY on the
modem and give another one to whoever requires access to it.
C. "We are automating our sales force as well as increasing our telecommuting
effort. Now the issue of security is increasing. We are running UNIX and considering NT.
I am told that since UNIX is very open, it is not very secure. Do you have anything in
that area?"
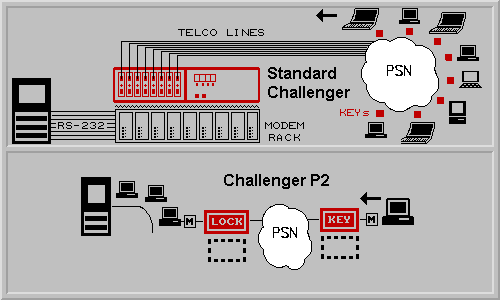
R. Log on to one of the hacker WEB sites and you can probably get about 50 pages of
methods of hacking UNIX or NT systems. To address this issue, we make a whole
family of hardware security devices called the CHALLENGERS.
They connect to the operative modems, and operate like Locks and Keys. The caller must
have the proper Key to be able to access a "Locked" modem. The LOCKs range from
small single line units up to larger 19" programmable rack mount units that can secure
up to 64 modems and provide detailed audit reports. The larger programmable models start
at $1195.00 and the smaller preprogrammed single line units cost $99.00 each. The KEYs
range from $99.00 to about $60.00 depending on the model and the quantities.
You may be able to use Caller ID to verify access for your telecommuters that call from
fixed locations. We have a product called the TLC that
can recognize both caller ID and the hardware Keys. So only the mobile users would
require the $79.00 hardware Keys. The TLC keeps a database of authorized codes and
provides excellent audit reports. The nice thing about all of the Challenger family
is that they operate on the analog side of the modems and are completely transparent
to the hardware, software, and the user; no additional codes to enter or other burden
on the caller. If you make it too cumbersome, the users will rebel and try to find
a way around it. Security does not have to be cumbersome. The TLC cost is $295.00.
Added July 10, 2001
C. "We configure our modems not to answer so they can only be used for
outbound calls, but the users have learned to reconfigure and use them
for outside access. Now we have open modems."
R. Put a CHALLENGER P2 lock on each
of the modems. It will reject all inbound calls since no Key exists for them.
Unless you want some of those too.
C. "How can I be sure that the passwords I give my contractors are not
spread around?"
R. Use a CAS and give them a one-time password
each time they have to call in. You could also designate a time limit in which
to call in.
R. Optionally, you could also use a SP-RRC and an
Intelligent AC power strip to power the modems ON when required.
C. "I use your K-RRC to turn remote
modems ON and OFF as required. What if someone quits and walks off with a Key?"
R. Buy a $99.00 Programmer then simply call all of the "controller sites"
(K-RRC). When they answer, they will automatically be
reprogrammed with a new code. Then you could also call the Keys or let them call the
programmer to get them reprogrammed. This is a very simple process.
C. "Ok, I can use a CHALLENGER P2 to
authenticate access, but I still don't want the callers to have access to my entire
network when they do call in."
R. Use a MINI FIREWALL also. When the modem
answers, the MFW will disconnect the network. Or you could elect to disconnect only
selected servers.
C. "Providing CHALLENGER P2 hardware
Keys to all of our potential callers can get a little pricey. What are some other
options that will offer some degree of security?"
R. You could consider the CHALLENGER TT. It
recognizes up to an eight-digit Touch-Tone password and you could reprogram it as
necessary. This places a little more burden on the users, but they don't need the Keys.
R. The TLC is also an option. It provides
security based on Caller ID. Your users wouldn't even have to know. You could program
up to 50 authorized CIDs into it. It will also recognize the hardware Keys if you have
some mobile users that may require them.
C. "I want to insure that any user calls me to get permission to access
our system."
R. There are several ways to accomplish this. The most obvious is with a
CAS. That is what it was built for. You could
also use a SP-RRC to power On the remote modem or even
a K-RRC. It is a rebooting device, but you could just
use it's security aspect. Basically the caller will call you first. If you have a
programmer attached to the line and the caller has a Key, the Key will be reprogrammed
during the initial call. You then call the K-RRC with your programmer to program it to
match the Key. This is really quite simple all you really need to do is flip one dip
switch then place the call and the hardware does the rest. (See Tech Tips
Monitoring Vendor Access.)
C. "This idea of keeping things turned OFF when you are not using them is
becoming more popular in the security industry. Are you perusing anything in that
area?"
R. You are preaching to the choir. This "age old wisdom" has recently been
rediscovered. We have a number of products that can accomplish that requirement. Most are
listed under our Rebooting Products. Since we make both security
products and the remote rebooting products, a lot of the secure authentication aspects are
also incorporated into the remote power ON/OFF products. There are a number of different
products and features that can be combined to meet a number of different objectives. They
range from simply turning power ON/OFF to a single modem to products that can control
the AC power to hundreds of different machines in a building.
PANIC
C. "I saw some methods to attack my software security on the Internet...
and they work. I need something else quick!"
C. "We have customer's information on our system. We found out that we are
liable for it. My boss said get something NOW!"
C. "One of our guys quit and has his PC and all of our passwords. I don't
trust him. I disconnected all of my modems. Can you ship me something overnight
that works right out of the box with no learning curve?"
R. Yes to the previous three comments. The CHALLENGER
LOCKS; plus we can drop ship the KEYs to your users.
C. "We are way behind in our schedule. We need some protection for our
access server now!.. until we get a better grasp on the security part of our
software, besides somebody said it didn't work anyway... full of bugs... an
after thought. We'll probably never get to it."
R. Put some CHALLENGERS on the system now. If you
ever get to the software, the CHALLENGER will only make it that much more secure.
DIAL BACK
C. "Our dial back modems only handle 10 dial back numbers. I never thought
we would get to this point, but we now have four modems and over 30 users. It's
a real juggling act."
C. "We provide a national on-line service and I don't want to pay toll
charges for the return call with dial back modems."
C. "The administration of dial back numbers is a hassle, it seems that
someone is always moving or being added or changed. I went nuts when they
changed our area code. Still getting complaints."
C. "Our dial back modems don't address our mobile sales force. What do you
have?"
R. CHALLENGER hardware KEYs will address the previous
four comments and without driving your road warriors crazy.
C. "Sometimes the modems don't train at their highest rate on the dial
back. I don't know why and I don't care. Some times it requires several tries.
It takes too long. What's your suggestion?"
R. CHALLENGERS of course, to all of the above.
They will allow or not allow the connection on the first call. No callbacks, retraining,
busy lines, etc.
C. "How can I get my home PC to dial me back?"
R. Install an SP-RRC switch and a power strip. Call
the SP-RRC and enter a Touch-Tone password and 'power on' command. Hang up and the PC
will dial you back, if configured correctly, at a predefined number. The SP-RRC can also
share the same home telephone line.
MAINTENANCE PORTS
C. "We use dial modems to manage all of our networks. Anyone can dial in
and reconfigure or monitor them."
C. "We have maintenance ports on a number of different products. We need
an overall solution to secure them. Right now, they basically have no security
on them at all."
C. "I heard that the passwords for the maintenance port on our phone
system has been leaked. I want to buy a solution for our maintenance company.
It's our money. If we get burned, we pay."
R. Your right. Put some CHALLENGER LOCKs on the
maintenance ports and give your maintenance company a KEY. It will allow them access
to your system on a secure basis while being transparent to them when accessing other
systems. Look at the CHALLENGER P2 BAS (Bi-level
Access System). It was originally designed for outside maintenance firms.
C. "We have some patient monitoring equipment that is accessed by dial
modems that we want to further protect. It's pretty hard to reconfigure it, but
it could be a critical health situation."
R. CHALLENGER LOCKS and KEYs will protect it.
Plus it makes for a better argument in court, should something ever happen.
C. "These maintenance ports are getting out of hand. Suddenly, it dawned
on me how many we have and how many companies (people) have access to our system."
R. You are right, the growth of maintenance ports is exploding. As such they are
also becoming a favorite path of entry for hackers and other pests. Plus, to save phone
lines one modem may provide access to several different machines. Our
232-PORT SHARING SELETION SWITCH addresses this
development. It requires a hardware KEY on the caller's modem before they can gain access
to the modem. Then, a rotary switch on the KEY provides automatic access to the RS-232
port to which they wish to connect. You can also program the KEY to only allow access
to selective ports so different groups only have access to their own ports.
On this same subject we also have another product, the
MODEM ROUTER SWITCH (MRS), that provides the same
port selection options except that they are modem ports instead of RS-232 ports.
C. "We only have one maintenance port to access, but we don't want to
put in a separate telephone line for it. What's the answer?"
R. The FTS is a $225.00 solution. It will allow
you to share a line. The normal calls go to it's default port. It also has two
alternate ports that the caller can access through a touch-tone password and port
selection. You can also get an AC power strip that can be controlled with
the same call.
C. "I heard that these maintenance techs often move to different
companies and often try to sabotage some of the accounts of their previous
employers."
R. That's true. The bottom line is that they are just people that are working
for these maintenance firms. But internal or external sabotage have the same results.
That is why you should insist that your maintenance modems be protected. Most often,
the maintenance companies don't care for this because it impedes their access and
requires additional effort to administer security. But it's your money.
C. "We have about 30 servers across the country. We automatically dial them
at night to upload and download files. They also have occasion to dial us during the
day. I noticed, from our logs that the lines are busy sometimes and sometimes the
servers are hung up. We use passwords and authorization codes, but it kind of worries
me to leave those modems "open" all of the time."
R. Add the CHALLENGER P2 to your modems.
Adding the hardware will increase your software security a thousand times. They will
prevent unauthorized callers from crashing your system or even stealing the data. One
of the nice features about the Challengers is that you don't have to have anyone
attending them when a call is made. Cost is $79.00 each.
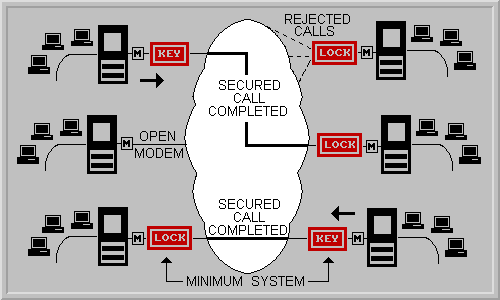
C. "The P2 Lock and Key concept is quite flexible, but suppose someone
steals a lock and uses it as a key to call other locks?"
R.That's the trade off, flexibility vs. security, but we can prevent the Locks
from making outbound calls. Just specify it when you order them.
C. "I have about 20 remote servers that I am trying to maintain remotely.
I would like to secure them and selectively restrict access to their maintenance ports to
various groups."
R. Look at the CHALLENGER P2 BAS (Bi-level
Access System). It provides two levels of access, which is normally enough for
most users. But you can also further define different groups by programming each
group with a different "random number code". However, the MASTER KEY would
have access to all of the groups.
HEALTHCARE
C. "Our doctors want to access patient histories from each of their
offices as well as from home. They want the access to be secure, but don't want
to go through any cumbersome sign-on rituals."
R. The CHALLENGER P2 is an ideal solution.
We have them installed in a similar application in a clinic. Within the clinic they
have access over the LAN but outside the office their dial access is secured by a
STANDARD CHALLENGER system. Don't forget about the
pharmacy and the lab, too.
C. "Our doctors our tying up our lines. They sign-on and stay on. Does
your system have a max call disconnect timer?"
R. Yes, plus we are playing with the idea that the max call time can be
programmed into the KEY so different KEYs can have different max call
times."
C. "We had a case where the doctor's passwords were being sold and used
for bogus prescriptions."
R. It is probably easier than stealing credit card numbers.
C. "We run an emergency response system. We want to verify the ID of the
caller. No time for sign-on codes."
R. We have incorporated Caller ID into some of our products. This may be a
solution. Look at the Telephone Line to Computer Interface (TLC).
THE COMPANY
C. "Who are you guys?"
R. We have been around for over 20 years. Primarily building communication
products. We built our first dial security product for a branch of the U.S. military
over six years ago. They apparently didn't care for any of the products that were
on the market at the time and definitely did not want to rely solely on a software
password solution. Their specs were quite stringent... minimal caller interaction,
no batteries, or touch keypad cards. In fact, they wanted unauthorized calls to be
defeated before the modems could even train and without human interaction. I guess
when you're inside the Washington Beltway; you become a target for every random
"kook" with a modem and a war dialer. No telling how many of them are
running at any time: scanning for modems. In any event, that solution became our
first dial security product. We still call it the
"STANDARD CHALLENGER". Since then we have
applied the "Challenge Response" technology to a number of other smaller
dial security products and incorporated it into some of our newer switching devices.
C. "What makes your products better than the other guys?"
R. Probably it's the way that we have blended ease of use with a level of
effectiveness. It is current technology that was simply not available several years
ago. Our products are deceptively simple to use and maintain and the price is right
too. One of the attendees at a recent Open Systems Conference in Orlando stopped by
the booth, reviewed the products, and comments that they were not "geekie"
enough for her. That was one of the best complements she could have given us and
that about sums up the designs objectives of the product line.
C. "Why haven't I heard of you?"
R. I don't know. We do some advertising, but this is a low profile type of
market and you have to respect your customer's privacy. It seems as though a lot
of this type of equipment is recommended by consultants. Since dial security is
not the hot issues of the time, they don't seem to keep on top of it. Instead they
fall back on concepts that they are familiar with that were developed 10 years
ago, these "security experts" are a pretty close knit group. Several fortune
500 companies use our products as well as a myriad of smaller companies.
| 



